
Red Teaming Vs Penetration Testing Guide
In the evolving cybersecurity landscape, organizations face a critical decision: Red Teaming or Penetration Testing? Both are essential security assessment methods, but they serve different purposes and target different organizational needs. Understanding the distinction can mean the difference between reactive vulnerability management and proactive threat defense.
Red Teaming Vs Penetration Testing Guide
In the evolving cybersecurity landscape, organizations face a critical decision: Red Teaming or Penetration Testing? Both are essential security assessment methods, but they serve different purposes and target different organizational needs. Understanding the distinction can mean the difference between reactive vulnerability management and proactive threat defense.
With cyber attacks expected to cost businesses $10.5 trillion globally in 2025, choosing the right cybersecurity assessment approach isn't just a technical decision-it's a business imperative. SecurityLit helps organizations navigate this choice by understanding their unique security maturity and objectives.
Understanding Penetration Testing: The Foundation of Security Assessment
Penetration testing is a systematic cybersecurity assessment that identifies vulnerabilities within your IT infrastructure using controlled attack simulations. Think of it as a security health check that focuses on finding and documenting specific weaknesses before malicious actors can exploit them.
Key Characteristics of Penetration Testing:
- Duration: Typically 3-6 weeks
- Scope: Focused on specific systems, networks, or applications
- Approach: Technical testing using automated tools and manual techniques
- Goal: Identify as many vulnerabilities as possible with remediation recommendations
- Methodology: Often uses "white box" approach with system knowledge
When SecurityLit Recommends Penetration Testing:
- Organizations building their initial security foundation
- Compliance requirements (PCI DSS, SOC 2, HIPAA)
- Regular security validation needs
- Budget-conscious security assessments
- Specific system or application focus
Ready to identify your security vulnerabilities?
SecurityLit's expert penetration testing services provide comprehensive vulnerability assessment with actionable remediation strategies.
Get Started TodayRed Teaming: Advanced Threat Simulation
Red Teaming goes beyond vulnerability identification-it simulates real-world cyber attacks to test your organization's overall security culture and defensive capabilities. Red teams operate like actual threat actors, using any means necessary to achieve specific objectives without detection.
Key Characteristics of Red Teaming:
- Duration: 3 weeks to several months
- Scope: Comprehensive organizational assessment including people, processes, and technology
- Approach: "Black box" methodology with no prior system knowledge
- Goal: Test detection and response capabilities while achieving specific objectives
- Methodology: Mimics real attacker tactics, techniques, and procedures (TTPs)
SecurityLit's Red Teaming Advantages:
- Tests incident response procedures
- Evaluates security awareness training effectiveness
- Assesses physical security measures
- Challenges existing security controls
- Provides realistic attack scenarios
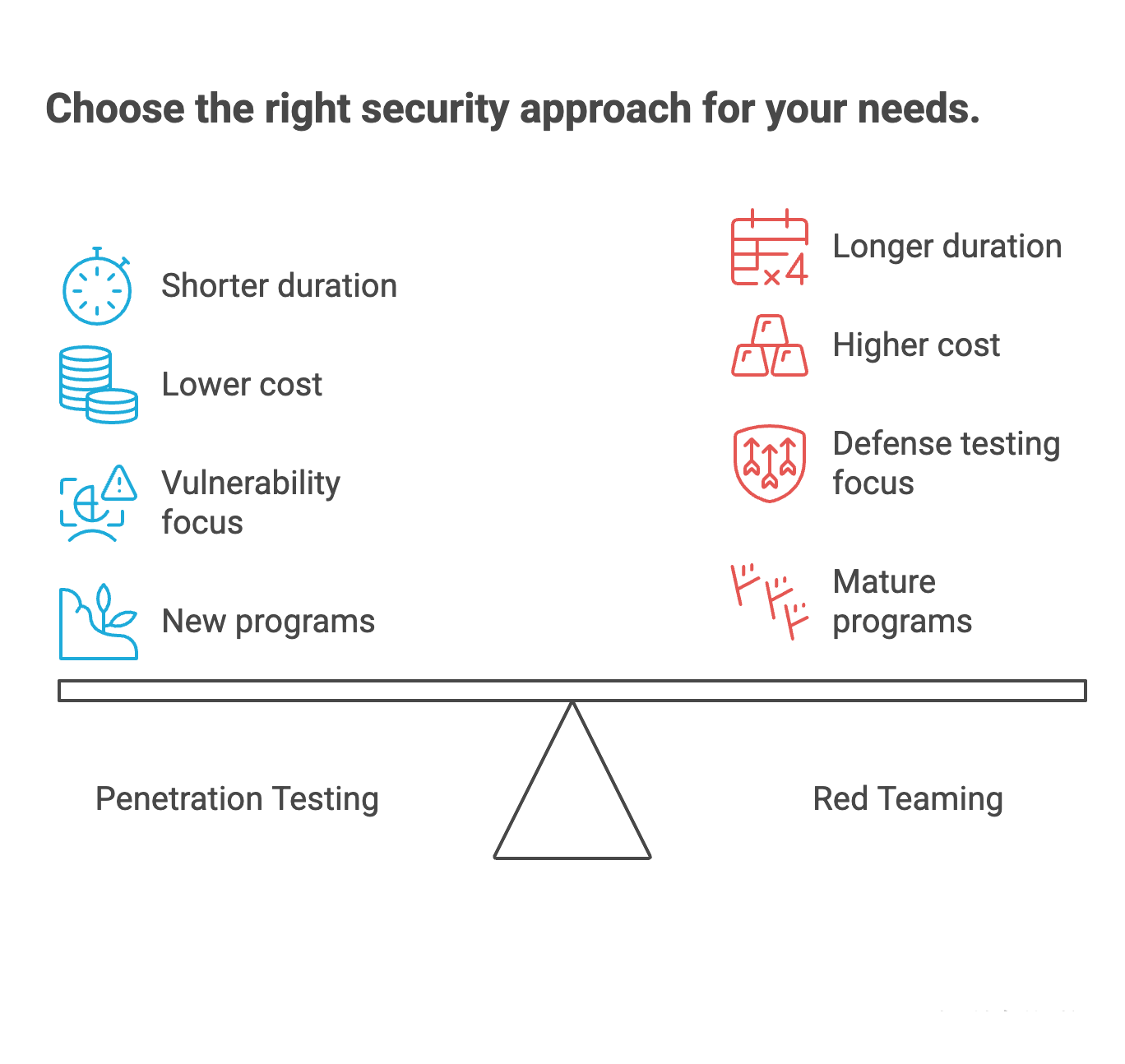
Red Team vs Penetration Testing Comparison
The Key Differences: Making the Right Choice
| Factor | Penetration Testing | Red Teaming |
|---|---|---|
| Primary Focus | Vulnerability identification | Overall security posture testing |
| Cost | More cost-effective | Higher investment due to scope |
| Timeline | 1-6 weeks | 3 weeks to months |
| Collaboration | High collaboration with IT teams | Minimal collaboration (stealth approach) |
| Detection Testing | Limited | Comprehensive blue team testing |
| Compliance Value | Strong for regulatory requirements | Advanced assurance validation |
Industry-Specific Considerations for SecurityLit Clients
Healthcare Organizations
Penetration Testing: Essential for HIPAA compliance and regular vulnerability management
Red Teaming: Critical for testing incident response to ransomware and advanced persistent threats
Financial Services
Penetration Testing: Required for PCI DSS compliance and regular security validation
Red Teaming: Valuable for testing fraud detection systems and advanced threat response
Manufacturing
Penetration Testing: Important for operational technology (OT) security assessments
Red Teaming: Crucial for testing supply chain attack scenarios and industrial espionage defenses
Professional Services
Penetration Testing: Regular assessments for client data protection validation
Red Teaming: Testing against targeted attacks on high-value client information
SecurityLit's Assessment Recommendation Framework
Choose Penetration Testing If:
- Building initial cybersecurity program
- Meeting compliance requirements
- Limited security assessment budget
- Focusing on specific systems or applications
- Need regular, systematic vulnerability identification
Choose Red Teaming If:
- Mature cybersecurity program with established controls
- Want to test incident response capabilities
- Previous penetration tests show minimal vulnerabilities
- Need advanced threat simulation
- Preparing for sophisticated threat actors
SecurityLit's Hybrid Approach
Most organizations benefit from a combined strategy: regular penetration testing for continuous vulnerability management, supplemented by periodic red team assessments for comprehensive security validation.
Unsure which assessment your organization needs?
Contact SecurityLit for a strategic cybersecurity consultation to determine the optimal testing approach for your security maturity and business objectives.
Contact SecurityLitThe SecurityLit Advantage: Expert Assessment Services
At SecurityLit, our cybersecurity assessment services include:
- Comprehensive Penetration Testing across web applications, networks, and cloud infrastructure
- Advanced Red Team Assessments with real-world attack simulation
- Hybrid Assessment Programs combining both methodologies for complete coverage
- Post-Assessment Strategic Guidance for remediation prioritization and security program enhancement
Conclusion
The choice between Red Teaming and Penetration Testing isn't either/or—it's about understanding your organization's security maturity, objectives, and threat landscape. SecurityLit's expert assessment services help organizations build robust security programs through strategic testing approaches tailored to their specific needs.
Whether you need foundational vulnerability assessment through penetration testing or advanced threat simulation via red teaming, SecurityLit provides the expertise and strategic guidance to strengthen your cybersecurity posture against evolving threats.
FAQs: Red Teaming vs Penetration Testing
Q: How do I know if my organization is ready for Red Teaming instead of Penetration Testing?
A: SecurityLit recommends Red Teaming when your organization has established basic security controls and regular penetration tests consistently find few critical vulnerabilities. If you're just starting your cybersecurity journey or need to meet specific compliance requirements, penetration testing provides the foundational assessment you need. Red Teaming is ideal for mature organizations wanting to test their detection and response capabilities against sophisticated attack scenarios.
Q: What's the typical cost difference between Red Teaming and Penetration Testing, and what should we budget for?
A: Penetration testing is generally more cost-effective, typically running 1-6 weeks with focused scope and methodology. Red Teaming requires higher investment due to its comprehensive nature, extended timeline (3 weeks to months), and broader resource requirements. SecurityLit provides flexible engagement models allowing organizations to start with penetration testing and graduate to red teaming as their security program matures, maximizing ROI while building robust defenses.

With cyber attacks expected to cost businesses $10.5 trillion globally in 2025, choosing the right cybersecurity assessment approach isn't just a technical decision-it's a business imperative. SecurityLit helps organizations navigate this choice by understanding their unique security maturity and objectives.
Understanding Penetration Testing: The Foundation of Security Assessment
Penetration testing is a systematic cybersecurity assessment that identifies vulnerabilities within your IT infrastructure using controlled attack simulations. Think of it as a security health check that focuses on finding and documenting specific weaknesses before malicious actors can exploit them.
Key Characteristics of Penetration Testing:
- Duration: Typically 3-6 weeks
- Scope: Focused on specific systems, networks, or applications
- Approach: Technical testing using automated tools and manual techniques
- Goal: Identify as many vulnerabilities as possible with remediation recommendations
- Methodology: Often uses "white box" approach with system knowledge
When SecurityLit Recommends Penetration Testing:
- Organizations building their initial security foundation
- Compliance requirements (PCI DSS, SOC 2, HIPAA)
- Regular security validation needs
- Budget-conscious security assessments
- Specific system or application focus
Ready to identify your security vulnerabilities?
SecurityLit's expert penetration testing services provide comprehensive vulnerability assessment with actionable remediation strategies.
Get Started TodayRed Teaming: Advanced Threat Simulation
Red Teaming goes beyond vulnerability identification-it simulates real-world cyber attacks to test your organization's overall security culture and defensive capabilities. Red teams operate like actual threat actors, using any means necessary to achieve specific objectives without detection.
Key Characteristics of Red Teaming:
- Duration: 3 weeks to several months
- Scope: Comprehensive organizational assessment including people, processes, and technology
- Approach: "Black box" methodology with no prior system knowledge
- Goal: Test detection and response capabilities while achieving specific objectives
- Methodology: Mimics real attacker tactics, techniques, and procedures (TTPs)
SecurityLit's Red Teaming Advantages:
- Tests incident response procedures
- Evaluates security awareness training effectiveness
- Assesses physical security measures
- Challenges existing security controls
- Provides realistic attack scenarios

Red Team vs Penetration Testing Comparison
The Key Differences: Making the Right Choice
| Factor | Penetration Testing | Red Teaming |
|---|---|---|
| Primary Focus | Vulnerability identification | Overall security posture testing |
| Cost | More cost-effective | Higher investment due to scope |
| Timeline | 1-6 weeks | 3 weeks to months |
| Collaboration | High collaboration with IT teams | Minimal collaboration (stealth approach) |
| Detection Testing | Limited | Comprehensive blue team testing |
| Compliance Value | Strong for regulatory requirements | Advanced assurance validation |
Industry-Specific Considerations for SecurityLit Clients
Healthcare Organizations
Penetration Testing: Essential for HIPAA compliance and regular vulnerability management
Red Teaming: Critical for testing incident response to ransomware and advanced persistent threats
Financial Services
Penetration Testing: Required for PCI DSS compliance and regular security validation
Red Teaming: Valuable for testing fraud detection systems and advanced threat response
Manufacturing
Penetration Testing: Important for operational technology (OT) security assessments
Red Teaming: Crucial for testing supply chain attack scenarios and industrial espionage defenses
Professional Services
Penetration Testing: Regular assessments for client data protection validation
Red Teaming: Testing against targeted attacks on high-value client information
SecurityLit's Assessment Recommendation Framework
Choose Penetration Testing If:
- Building initial cybersecurity program
- Meeting compliance requirements
- Limited security assessment budget
- Focusing on specific systems or applications
- Need regular, systematic vulnerability identification
Choose Red Teaming If:
- Mature cybersecurity program with established controls
- Want to test incident response capabilities
- Previous penetration tests show minimal vulnerabilities
- Need advanced threat simulation
- Preparing for sophisticated threat actors
SecurityLit's Hybrid Approach
Most organizations benefit from a combined strategy: regular penetration testing for continuous vulnerability management, supplemented by periodic red team assessments for comprehensive security validation.
Unsure which assessment your organization needs?
Contact SecurityLit for a strategic cybersecurity consultation to determine the optimal testing approach for your security maturity and business objectives.
Contact SecurityLitThe SecurityLit Advantage: Expert Assessment Services
At SecurityLit, our cybersecurity assessment services include:
- Comprehensive Penetration Testing across web applications, networks, and cloud infrastructure
- Advanced Red Team Assessments with real-world attack simulation
- Hybrid Assessment Programs combining both methodologies for complete coverage
- Post-Assessment Strategic Guidance for remediation prioritization and security program enhancement
Conclusion
The choice between Red Teaming and Penetration Testing isn't either/or—it's about understanding your organization's security maturity, objectives, and threat landscape. SecurityLit's expert assessment services help organizations build robust security programs through strategic testing approaches tailored to their specific needs.
Whether you need foundational vulnerability assessment through penetration testing or advanced threat simulation via red teaming, SecurityLit provides the expertise and strategic guidance to strengthen your cybersecurity posture against evolving threats.
FAQs: Red Teaming vs Penetration Testing
Q: How do I know if my organization is ready for Red Teaming instead of Penetration Testing?
A: SecurityLit recommends Red Teaming when your organization has established basic security controls and regular penetration tests consistently find few critical vulnerabilities. If you're just starting your cybersecurity journey or need to meet specific compliance requirements, penetration testing provides the foundational assessment you need. Red Teaming is ideal for mature organizations wanting to test their detection and response capabilities against sophisticated attack scenarios.
Q: What's the typical cost difference between Red Teaming and Penetration Testing, and what should we budget for?
A: Penetration testing is generally more cost-effective, typically running 1-6 weeks with focused scope and methodology. Red Teaming requires higher investment due to its comprehensive nature, extended timeline (3 weeks to months), and broader resource requirements. SecurityLit provides flexible engagement models allowing organizations to start with penetration testing and graduate to red teaming as their security program matures, maximizing ROI while building robust defenses.
